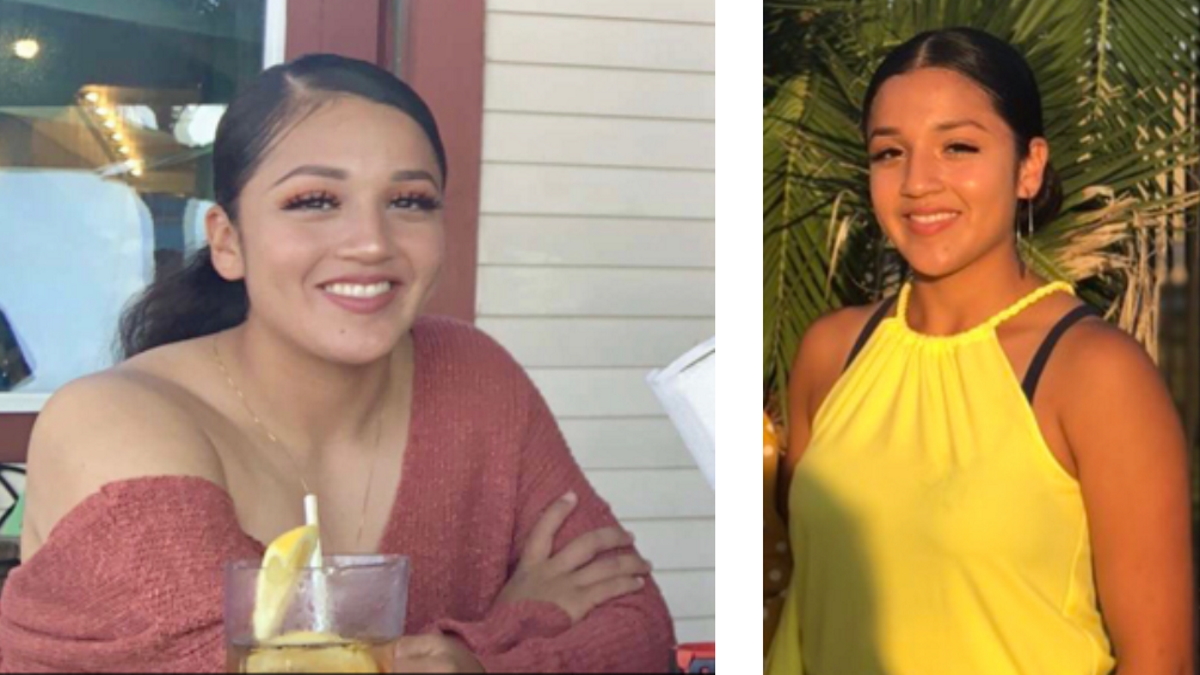The U.S. Army Criminal Investigation Command is offering a reward of up to $25,000 for credible information leading to the whereabouts of missing Fort Hood Soldier, Pfc. Vanessa Guillen.
The 20-year-old Vanessa Guillen was last seen April 22 between 11:30 a.m. and 12:30 p.m. in the parking lot of her Regimental Engineer Squadron Headquarters, 3rd Cavalry Regiment on Fort Hood, Texas and has not been heard from since that date.
Her car keys, barracks room key, identification card and wallet were later found in the armory room where she was working earlier in the day. She was last seen in the parking lot wearing a black t-shirt and purple fitness-type pants.
Originally from Houston, Texas, Pfc. Guillen maintained close ties with her family and the city of her birth, visiting there frequently while stationed at Fort Hood.
Guillen is of Hispanic descent, five feet, two inches tall, 126 pounds, with black hair and brown eyes. Her Military Occupational Specialty is a 91F, Small Arms/Artillery Repairer. She is an avid runner.
At this point, investigators have no credible information or report that Vanessa Guillen was sexually assaulted or that this case is in any way connected to the investigation into the disappearance of PV2 Gregory Wedel-Morales, who was last seen on the night of Aug. 19, 2019 while driving his car in Killeen, Texas.
Both of these allegations have been widely circulated via the media and on social media.
“We are completely committed to finding Vanessa and aggressively going after every single piece of credible information and every lead in this investigation,” said Chris Grey, spokesman for Army CID. “We will not stop until we find Vanessa.”
More than 150 people have been interviewed and “We are working very closely with multiple law enforcement agencies to include the FBI, Belton Police Department and the Texas Department of Public Safety, as well as others,” Grey said. “We have also partnered with Texas EquuSearch and the National Center for Missing and Exploited Children to tap into their resources as well. We have participated in ground and air searches on Fort Hood and throughout the Central Texas region.”
Army CID and Fort Hood continue to seek the public’s help for information.
“We know somebody out there has some very critical information pertaining to this investigation and we strongly encourage you to do the right thing and come forward,” Grey said. “Do it for Vanessa and do it for her family, friends and fellow Soldiers.”
Persons with information can contact Army CID Special Agents at 254-287-2722 or the Military Police Desk at 254-288-1170.
They can also anonymously submit information at https://www.cid.army.mil/report-a-crime.html.
People wishing to remain anonymous will be honored to the degree allowable under the law and the information will be held in the strictest confidence allowable.
For more information about CID or to report a crime, visit www.cid.army.mil.
Fort Hood Press Center (June 2020) Reward Increased: Missing Fort Hood Soldier